BSQL Hacker
10 SQL Injection Tools
BSQL Hacker is developed by Portcullis Laboratory. BSQL Hacker is an automatic SQL injection tool (supporting blind SQL injection). Its design purpose is to inject SQL overflow into any database. BSQL Hacker applies to people who have experience injecting users and those who want to automate SQL injection. BSQL Hacker can automatically attack Oracle and MySQL databases, and automatically extract the data and architecture of the database.
JSQL Injection is a lightweight application used to find database information from a distant server. It is free, open source and cross-platform (Windows, Linux, Mac OS X). Kali Linux logo jSQL Injection is also part of the official penetration testing distribution Kali Linux and is included in distributions like Pentest Box, Parrot Security OS. Havij is an automated SQL Injection tool that helps penetration testers to find and exploit SQL Injection vulnerabilities on a web page. It's a fully automated SQL Injection tool and it is distributed by ITSecTeam, an Iranian security company. The name Havij means “carrot”, which is the tool’s icon. The tool is designed with a user-friendly GUI that makes it easy for an operator to. Download BSQL Hacker BSQL (Blind SQL) Hacker is an automated SQL Injection Framework / Tool designed to exploit SQL injection vulnerabilities virtually in HACKINGHEART: HACKING DEMYSTIFIED IN THIS SITE U WILL GET LOTS OF TECH NEWS/ANTIHACKING/IT SECURITY/PROGRAMMING TIPS,LATTEST HAPPENING ON IT AND SOFTWARE etc.

Download Bsql Hacker Windows 10
The Mole
10 SQL Injection Tools
The Mole is an open source automated SQL injection tool that bypasses IPS/IDS (intrusion prevention system/intrusion detection system). It can detect injection points and exploit them by providing only a URL and an available keyword. The Mole can use union injection technology and logical query-based injection technology. The Mole attacks include SQL Server, MySQL, Postgres and Oracle databases.
Pangolin
10 SQL Injection Tools
Pangolin is a security tool that helps penetration testers perform SQL Injeciton testing. Pangolin and JSky (Web Application Security Vulnerability Scanner, Web Application Security Assessment Tool) are products of NOSEC. Pangolin has a friendly graphical interface and supports testing almost all databases (Access, MSSql, MySql, Oracle, Informix, DB2, Sybase, PostgreSQL, Sqlite). Pangolin can achieve maximum attack testing results through a series of very simple operations. It gives the test steps from the beginning of detection injection to the end of control target system. Pangolin is currently the most widely used security software for SQL injection testing in China.
Sqlmap
10 SQL Injection Tools
Sqlmap is an automatic SQL injection tool. It is competent to implement a wide range of database management system back-end fingerprints.
Retrieve the DBMS database, usernames, tables, columns, and list the entire DBMS information. Sqlmap provides the ability to dump database tables and MySQL, PostgreSQL, and SQL Server servers to download or upload any file and execute arbitrary code.
Havij
10 SQL Injection Tools
Havij is an automated SQL injection tool that helps penetration testers discover and exploit SQL injection vulnerabilities in Web applications. Havij can not only automatically mine available SQL queries, but also identify the type of background database, the user name and password hash of retrieved data, dump tables and columns, extract data from the database, and even access the underlying file system and execute system commands, provided that there is an available SQL injection vulnerability. Havij supports a wide range of database systems, such as MsSQL, MySQL, MSAccess and Oracle. Havij supports parameter configuration to avoid IDS, proxy and background landing address scanning.
Enema SQLi
10 SQL Injection Tools
Enema SQLi is different from other SQL injection tools. Enema SQLi is not automatic. It requires some knowledge to use Enema SQLi. Enema SQLi can use user-defined queries and plug-ins to attack SQL Server and MySQL databases. Support injection attacks based on error-based, Union-based and blind time-based.
SQLninja
10 SQL Injection Tools
Download Bsql Hacker Download
The software of SQLninja is written in Perl and conforms to GPLv2 standard. The goal of SQLninja is to exploit SQL injection vulnerabilities in Web applications, which rely on Microsoft’s SQL Server as backend support. Its main goal is to provide a remote shell on a vulnerable database server, even in an environment with strict precautions. After an SQL injection vulnerability has been discovered, enterprise administrators, especially testers of penetration attacks, should use it to automatically take over the database server. There are many other SQL injection vulnerability tools on the market, but unlike other tools, SQLninja does not need to extract data, but focuses on obtaining an interactive shell on a remote database server and using it as a foothold in the target network.
sqlsus
10 SQL Injection Tools
Download Bsql Hacker Server
Sqlsus is an open source MySQL injection and takeover tool. sqlsus is written in Perl and based on the command line interface. Sqlsus can get the database structure, inject your own SQL statements, download files from the server, crawl the web site writable directory, upload and control the backdoor, clone the database and so on.
Safe3 SQL Injector
10 SQL Injection Tools
Safe3 SQL Injector is one of the most powerful and easy-to-use penetration testing tools, which can automatically detect and exploit SQL injection vulnerabilities and database server processes. Safe3 SQL Injector has the ability to read MySQL, Oracle, PostgreSQL, SQL Server, Access, SQLite, Firebird, Sybase, SAP MaxDB and other databases. It also supports writing files to MySQL, SQL Server, and executing arbitrary commands in SQL Server and Oracle. Safe3 SQL Injector also supports error-based, Union-based and blind time-based injection attacks.
SQL Poizon
10 SQL Injection Tools
The graphical interface of SQL Poizon enables users to attack without deep expertise. The built-in browser of the SQL Poizon Scan Injection Tool helps to see the impact of injection attacks. SQL Poizon makes full use of the search engine “dorks” to scan sites with SQL injection vulnerabilities in the Internet.
The above is the whole content of this article. I hope it will be helpful to everyone’s study, and I hope you will support developpaer more.
TRANSCRIPT
BSQL HackerFerruh Mavituna (ferruh@mavituna.com)BSQL HACKER BSQL HACKERQuick Start BSQL Hacker for Anyone BSQL Hacker for Advanced Users Some Action Example: Supported Databas es for SQL Injection Wizard SQL Injection Wizard Injection in Querystring Injection from Raw Request Finish SQL Injection Using Attack Files and Attack File Templates What is an Attack File? What is an Attack File Template? How to use Attack Files? Attack File Features Key Features Requirements Security Issues Related with BSQL
1 55 5 6 6 7 8 8 10 10 12 12 12 12 13 13 14 15 16
1
Update Rep ository GUI Functions Automated Attacks Case Sensitive Magic Variables Generic Part: {X} {INJECTION} Blind SQL Injection Related: {CHAR} {POSITION} {OPERATION} Error Based SQL Injection: {ERROR_POSITION} {ERROR_BUFFER} Full Blind SQL Injection Related {SECONDS} Other {TOKEN}
16 17 17 17 18 18 18 18 18 18 18 18 18 18 18 19 19 19 19
BSQL HACKER CONSOLERequest Related Parameters Post Request Add Post Data -ap, --addpost Add Post Data File -apf, -addpostfile Add Post Request File -aprf, -addpostrequestfile Get Request
2020 20 20 20 20 21
2
Query -q, --query Cookies Add Cookie -ac, --addcookie Add Cookie Request File -acrf, -addcookierequestfile Headers Add Header -ah, --addheader Connection Related Parameters Threading Thread Count -t, --thr eadcount Start Delay -sd, --startdelay Miscellaneous Enable Automatic Redirects -ar, --allowredirect Request Timeout -rt, --r equesttimeout Proxy Related Enable Proxy -ep, --enableproxy Proxy URL -p, --proxy Authentication Related Default Network Credentials -dc, --defaultcredentials Username -u, --username Password -pwd, --password Domain Name -m, --domain Error Handling Error Retry -er, --errorretry Error Retry Sleep -ers, --errorretrysleep Injection Related Magic Variables Disable Confirm Found Char -dcfc, --dconfirmfoundchar
21 21 21 21 22 22 23 23 23 23 23 23 24 24 24 25 25 25 25 25 26 27 27 27 27 27 28
3
Length -l, --length Start Position -sp, --startposition Detection Related Detection Mode -dm, --detectionmode [time | search | deep] Detection Time -dt, --detectiontime Search String True -sst, --searchstringtrue Search String False -ssf, --searchstringfalse RegEx Support for Search -rx, --regex Session Token Support Related Parameters Token URL -turl, --tokenurl Token Extract RegEx -tex, --tokenr egex Disable Token Session Share -dtss, --disabletokensessionshare -tsr, --tokensamerequest BSQLHacker Related Parameters Silent (ALPHA) -s --silent Output (ALPHA) -o --output Matrix Sucks (ALPHA) -msux, --matrixsucks Help (ALPHA) -h, --help, -? Examples Known Issues
29 29 29 29 30 31 31 31 33 34 34 34 34 35 35 35 36 36 37 38
4
BSQL HackerBSQL (Blind SQL) Hacker is an automated SQL Injection Framework / Tool designed to exploit blind SQL injection vulnerabilities virtually in any database.
BSQL Hacker aims for experienced users as well as beginners who want to automate Blind SQL Injections.
If you dont want read lots of stuff stick with Quick Start guide and Videos .
Quick StartIf you already good with SQL Injections and just looking for a new tool to automate your attacks, you may just dive into Attack Files and understand the whole automation system, if you are not, you can try Attack File templates and SQL Injection Wizards.
BSQL Hacker for AnyoneIf you just want to exploit it by pressing play button keep reading, if not try BSQL Hacker for Advanced Users to understand how you can write your very own injections.
There are 3 ways to launch an exploit: 1. SQL Injection Wizard (no-brainer mode) 2. Loading an Attack Templates or an Exploit (easy) 3. Supplying custom injection (requires good SQL Injection knowledge)
In most of the common cases Templates and Wizard should be enough but you may want to do some advanced tricks or bypass some strange restriction. Then you need to supply your very own injections. After you come up with a new injection you can save / share it as Attack File Template.

5
You can always start by trying SQL Injection Wizard. It allows you to start a new attack from Raw Request or a simple URL. Itll test your injection for supported databases (see Supported Databases for SQL Injection Wizard). After you get it work you can modify settings and resume it.
If it doesnt work and you know the reason you can just fix it in the GUI and start the attack again.
If you are confident about it instead Wizard you may want to load a related Attack Template and just run it.
BSQL Hacker for Advanced UsersAs you know Blind SQL Injection is all about True and False responses. To able to write your very own attack files or handling some strange attacks you need to know following subjects quiet well: Blind SQL Injection Your target database functions Using Binary Search in Blind SQL Injection
If you dont know these, you can still use BSQL Hacker by wizards and templates. Please refer to BSQL Hacker for Anyone. Some Action BSQL Hacker relies on Magic Variables to automate attacks. In a Blind SQL Injection you have got couple of dynamic parameters: Position : {POSITION}
Comparison Operator : {OPERATION} Char to Compare : {CHAR}
These magic variables will be replaced on the fly by BSQL Hacker before sending the server. This allows automating lots of attacks easily. 6
Example: A sample Blind SQL Injection attack for MSSQL:
http://www.example.com/default.asp?p=1 AND ISNULL(ASCII(SUBSTRING(CAST(( USER)AS varchar(8000)), {POSITION},1)),0) {OPERATION}{CHAR}--
When you give this input to BSQL Hacker it will replace POSITION, OPERATION and CHAR with required values in the real time.
Following injections will send to the server:
Getting one character;1 AND ISNULL(ASCII(SUBSTRING(CAST((USER)AS varchar(8000)),1,1)),0)> 78 1 AND ISNULL(ASCII(SUBSTRING(CAST((USER)AS varchar(8000)),1,1)),0)< 78 1 AND ISNULL(ASCII(SUBSTRING(CAST((USER)AS varchar(8000)),1,1)),0)> 54 1 AND ISNULL(ASCII(SUBSTRING(CAST((USER)AS varchar(8000)),1,1)),0)> 54 1 AND ISNULL(ASCII(SUBSTRING(CAST((USER)AS varchar(8000)),1,1)),0)> 66 1 AND ISNULL(ASCII(SUBSTRING(CAST((USER)AS varchar(8000)),1,1)),0)> 72
Next Character;1 AND ISNULL(ASCII(SUBSTRING(CAST((USER)AS varchar(8000)),2,1)),0)>78 1 AND ISNULL(ASCII(SUBSTRING(CAST((USER)AS varchar(8000)),2,1)),0)>103 1 AND ISNULL(ASCII(SUBSTRING(CAST((USER)AS varchar(8000)),2,1)),0)>114
Above, you clearly see how magic variables are changing. Now if we want to port this attack to ORACLE we can come up with following attack:
7
http://www.example.com/default.asp?p=1 AND NVL(ASCII(SUBSTR((SELECT user FROM dual)),{POSITION},1)),0){OPERATION}{CHAR}
Obviously you can write similar attacks for other databases. BSQL ships with following ready to go files (Attack File Templates):
PostgreSQL SQL Server MySQL ORACLE
If you write an attack file template for another database which is not listed her e, please send it to me and itll be in the update repository quite soon for every user.
Supported Databases for SQL Injection Wizard MS SQL Server 2000 / 2005 and potentially others ORACLE MySQL
SQL Injection WizardTo able to use SQL Injection Wizard you should know vulnerable parameter or place.
If you know the vulnerable place / parameter youve got two options; New SQL Injection from Querystring New SQL Injection from Raw Request
8
Figure 1 : Injection Wizard
1. Run Injection Wizard (Ctrl + N) 2. Choose one of the following methods; a. If you can exploit it with a simple GET choose Injection in Querystring b. If its in POST, some HTTP Header or it does require a cookie (like authentication cookie) then choose From Raw Request
9
Injection in Querystring Now all you need to do is paste your URL and check vulnerable parameter from the list and click Finish.
Its critical that you leave default value for vulnerable parameter. Dont put single quote or similar stuff, just keep the original value.
Figure 2 : Injection Wizard - Injection Querystring
Injection from Raw Request If you want to supply your injection point from HTTP Raw Request, paste your request (from your proxy or something), point your cursor to injection place and then click Insert Injection Point button. This will put a {X} magic variable to vulnerable place.
10
You should supply the raw HTTP request done by browser to proxy which means request should include full URL of target like:
POST http://example.com/?p=1 HTTP/1.1
instead of
POST /?p=1 HTTP/1.1
Now you need to click finish to start SQL Injection.Its critical that you leave default value for vulnerable parameter. Dont put single quote or similar stuff, just keep the original value.
This is a good example of correctly marked HTTP raw request:GET http://example.com/?product_id=1{X} HTTP/1.1 Host: 192.168.2.55 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en -GB; rv:1.8.1.9) Gecko/20071025 Firefox/2.0.0.9 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q=0.9,text/plain;q=0.8,image/p ng,*/*;q=0.5 Accept-Language: en-gb,en;q=0.5 Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Connection: close Proxy-Connection: close Cookie: ASPSESSIONIDQQGQGKFU=OFLJAGDCEEEJFIBPCAODLAGP Pragma: no-cache Cache-Control: no-cache
11
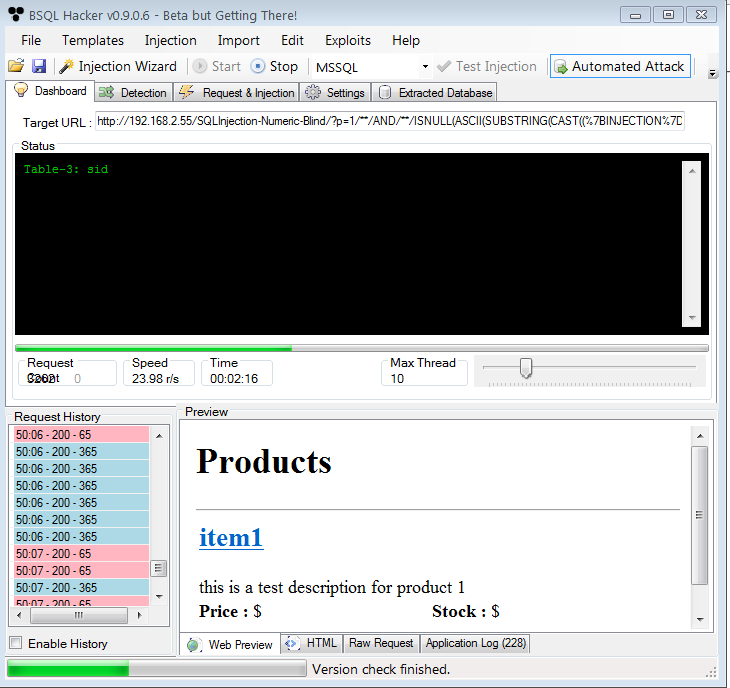
Finish SQL Injection When you click Finish BSQL Hacker will attempt to run injection and if it success it will let you know and start auto injection process. If you dont want auto injection you may stop the process, change settings and run it again.
Figure 3 : Testing for SQL Injection
Using Attack Files and Attack File TemplatesWhat is an Attack File?
Figure 4